One of the most important challenges that enterprises face today is protecting valuable data in their servers‚ hardware devices and other platforms. We are all well aware of the consequences that failing to do so can bring; data privacy breaches in companies such as Talk Talk and Sony are a cautionary tale for businesses of all sizes.
The Landscape
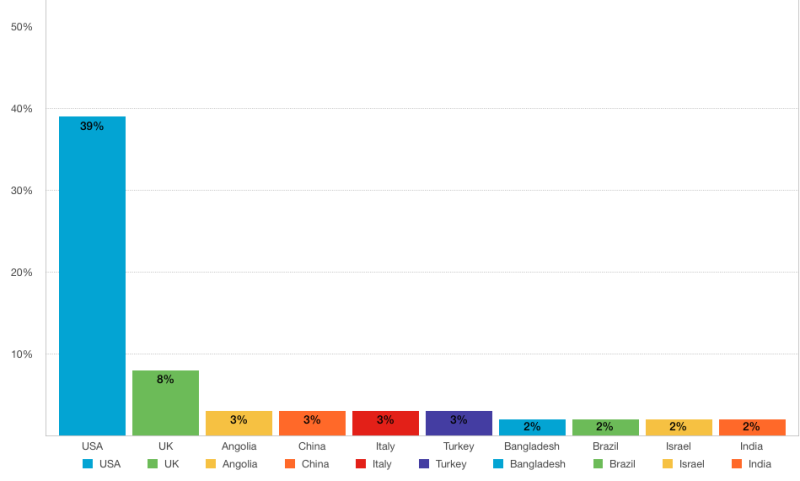
Global data demonstrates a surge in cyber crimes in recent years‚ from 16‚838 in 2000 to a staggering 262‚813 by 2013. This spike has been largely due to stolen and/or hacked identifications by numerous methods‚ including radio frequency IDs‚ smart cards‚ interactive tokens and more. The increasing threat of cyber crime calls for new‚ innovative methods for data protection and the next phase of identification.
Country Trends of Cybercrime as of December 2013
Recent advancements in mobile and smartphone technology have enabled dual mode authentication. The first step to access is a password or pin‚ followed by a second mode of authentication through the user’s device‚ which basically generates a code or a “one-time password’. Whilst this is a vast improvement in security‚ this mode of authentication is not fully secured; there is always a possibility of losing the device. This method is also rendered useless if the user is not carrying his or her device; it makes no sense for a password code to be sent to their home in New York when the user is travelling in Peru.
Embracing biometrics – the next digital identification for a secure future:
Imagine a world without passwords‚ codes or pins‚ where our bodies become passwords for the actions we undertake. The Washington Post recently quoted “Your human body will be your own key‚ and you will get an extremely customized experience on your device and feel more comfortable doing more on your device than ever before.” Companies engaged in safeguarding our data today are developing solutions that put the human body in perspective and make security look cooler through biometric technology.
Biometric data is personally identifiable information using physiological or behavioural traits‚ for authenticating devices or secure areas. These traits are universally present‚ unique to every individual and present for many years‚ with an ability to be measured. Most commonly identified traits include fingerprints‚ voice recognition‚ gait‚ hand or palm‚ iris‚ keystroke and signature/writing. Biometrics today are catching on rapidly in the area of security‚ to protect vital information from falling into the wrong hands.
Fingerprint recognition:
![[object Object] [object Object]](http://images.ctfassets.net/o6514hijae09/64fXxP0ssvZZ2BmKGaBwac/02c335fbb44fe84cb899f385f59a0e7f/fingerprint_ID.jpg)
Source: Flickr
Fingerprint recognition technology uses the pattern of ridges and valleys on the surface of the fingerprint to identify the user. It is highly reliable‚ robust‚ accurate and distinctive‚ as well as convenient to use. However‚ whilst the fingerprint is a stable trait‚ this technology isn’t without its defects. If the fingertips are dirty or have faced injury‚ for example‚ fingerprint capturing could be undermined.
Today‚ many enterprises are building small and portable devices that authenticate devices and data through a simple touch of the finger. User identification in mobiles‚ PDA’s and other personal devices is done conveniently through an in-built sensor (captive or thermal)‚ making it easier to develop such technologies on a mass scale.
Voice or speech recognition:
Voice identity requires a microphone to capture the voice of the speaker‚ before being processed by an external authentication server. Phone banking and the services industry utilise this technology to verify and authenticate users during the course of a conversation. Apart from a secure login‚ the technology allows hands-free authentication for devices and applications but people can use technology to mimic a voice or the system may get confused while processing certain voice commands. As the voice recognition is not 100 percent reliable‚ it should only be used as a secondary authentication.
The Iris scan technology:
![[object Object] [object Object]](http://images.ctfassets.net/o6514hijae09/5EGHTLe1RExGLCoJYk1KbD/b4ab18d81e44c552ba09fc810b59478e/16029123330_347b907c61_z.jpg)
Source: Flickr
This form of biometric technology seems worthy of science fiction‚ using the iris in the human eye for individual identification. The pattern generated by the fibres in the stroma‚ a pigmented layer in the iris‚ is unique to every individual. Smartphones today have enhanced processors‚ which allow you to integrate or develop new algorithms for biometric identification of the iris.
However‚ this cutting edge technology is not without its flaws. To work correctly‚ the device would need a high-quality camera and a near-infrared light. Currently‚ frontal cameras and front-facing shooters in Android and iOS devices simply aren’t high enough quality to view the iris well. Smartphone manufacturers will need to find a way to squeeze in the near-infrared light‚ whilst ensuring that it operates fast enough to avoid draining battery life and irritating users.
The future of biometric technology:
![[object Object] [object Object]](http://images.ctfassets.net/o6514hijae09/47Uhp38WDKV2kMgUUZLjxb/05deeafbf7434f18bde0bec06cbb9b01/11844737525_9ddca15708_z.jpg)
Source: Flickr
In the not-too-distant future‚ we could expect to see cars that would use fingerprint and voice recognition to start engines and direct turns and stops‚ all hands-free. We can expect tablets to measure our pupil dilation to gauge our attention span. Wearables like headbands‚ socks and bras could calculate our brain waves‚ heart rate and sweat levels to determine or predict illness and disease.
Biometrics technology‚ which was once used solely for measuring fitness-related activities‚ has today crept into mainstream consumer devices. The uprising trend could very well represent the next wave of mobile computing after smartphones‚ weaving biometrics technology into more aspects of everyday life.
References:
The future of authentication Biometrics‚ multi-factor‚ and co-dependency
Will we embrace biometrics to replace passwords? FIDO authentication at CES 2014The FIDO Alliance Announces FIDO Ready Certification and Authentication Products on Display at the 2014 International Consumer Electronics Show.